Reversing one thousand binaries
This past week (Nov 3rd) I attended the Hackfest CTF in Quebec city, QC. This was my second CTF and was the fist time I ever found a flag. This is how I found it.
The challenge began with a vague message "Reverse 1,000 binaries" and a link to download a zip file. It had 1,000 files named binary0, binary1, binary2... binary999.
The first thing I did was to try to run the first binary but I got a "Segmentation fault" error:
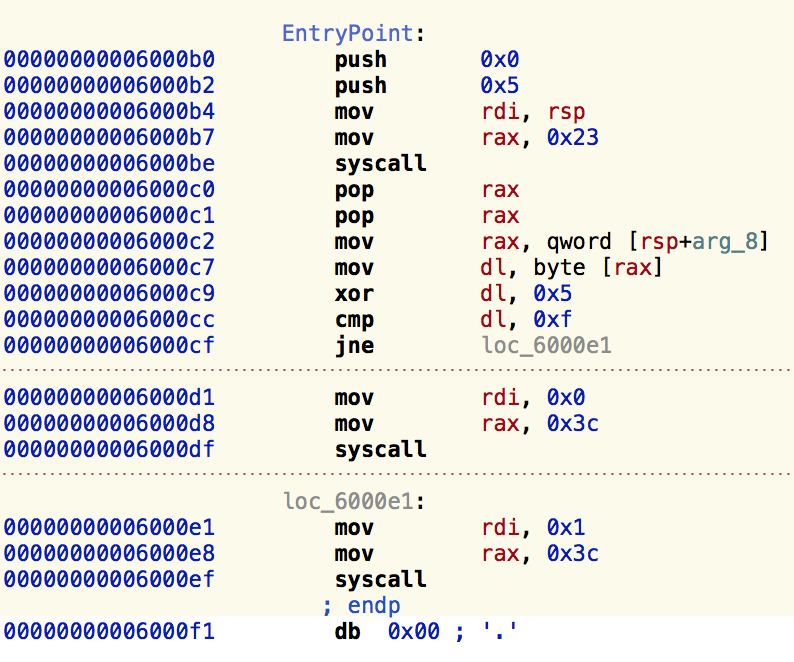
Then I opened the first binary in hopper and saw it was a very small binary, I opened the second and it was almost the exact same assembly code:
binary0
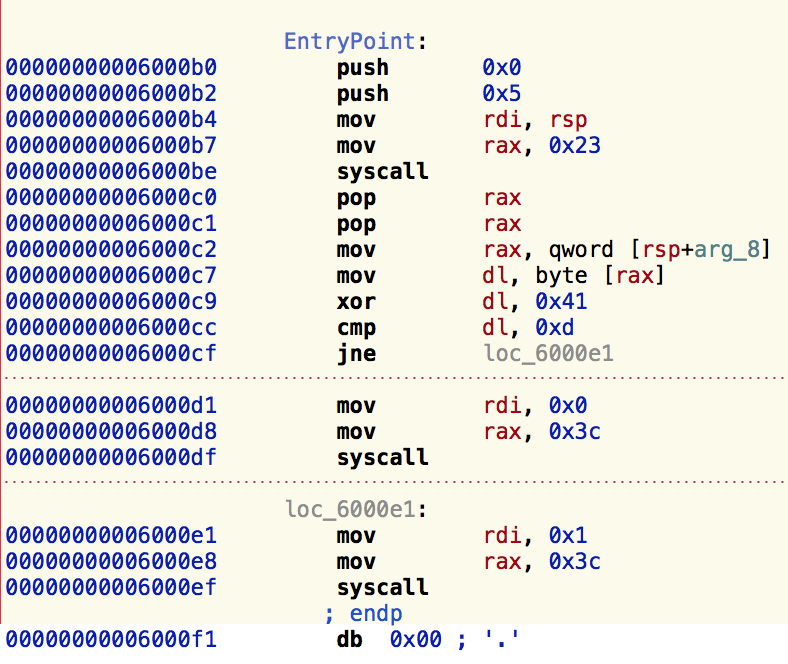
binary1
I assumed they were all part of one big binary and they where divided in 1k sub-binaries. My next idea was to figure how to combine all of them into just one binary; googling a bit I found that people suggested using cat but it didn't work for me.
cat binary0 binary1 ... binary999 > complete_binary
But looking closely to the assembly code I realized I didn't need to combine the binaries and execute them, since they all were pretty much the same, I just needed to understand what was changing. I saw the first binary had an xor operation between dl and 0x5 and then it was comparing it to 0xf. The second binary had the same operations but xor-ing dl and 0x41 and comparing it to 0xd. basically:
dl xor 0x05 = 0x0f
and
dl xor 0x41 = 0x0d
This meant that all I needed to do was to dump the assembly code of all the binaries and xor the static values to get the initial input: 0x5 xor 0xf = value_0, 0x41 xor 0xd = value_1
To do this I used objdump with the intel architecture for easier parsing:
objdump -x86-asm-syntax=intel -d binary0
Then I built a python script to automate this task, dumping the binary assembly code, parsing it and computing the xor values.
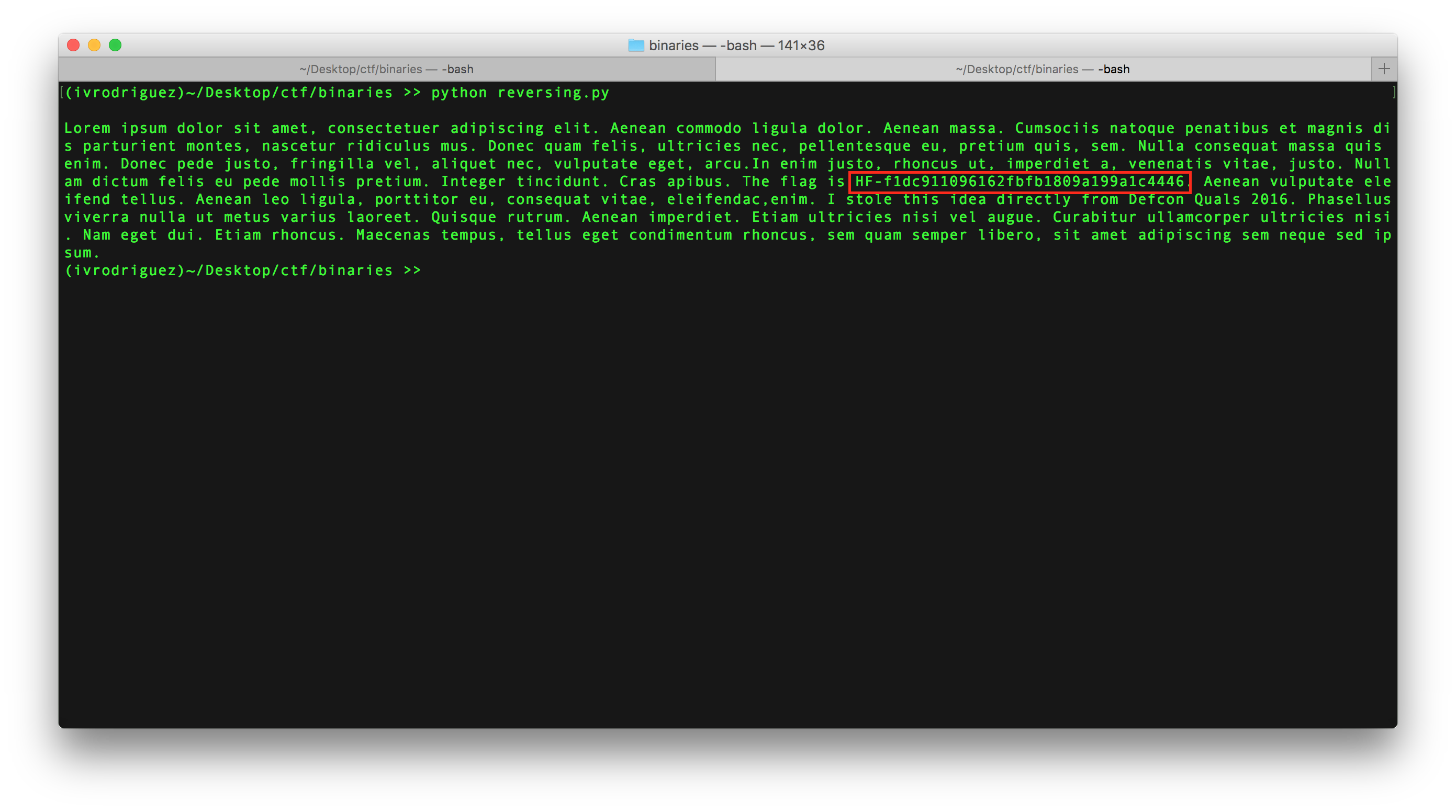
And this is the result:
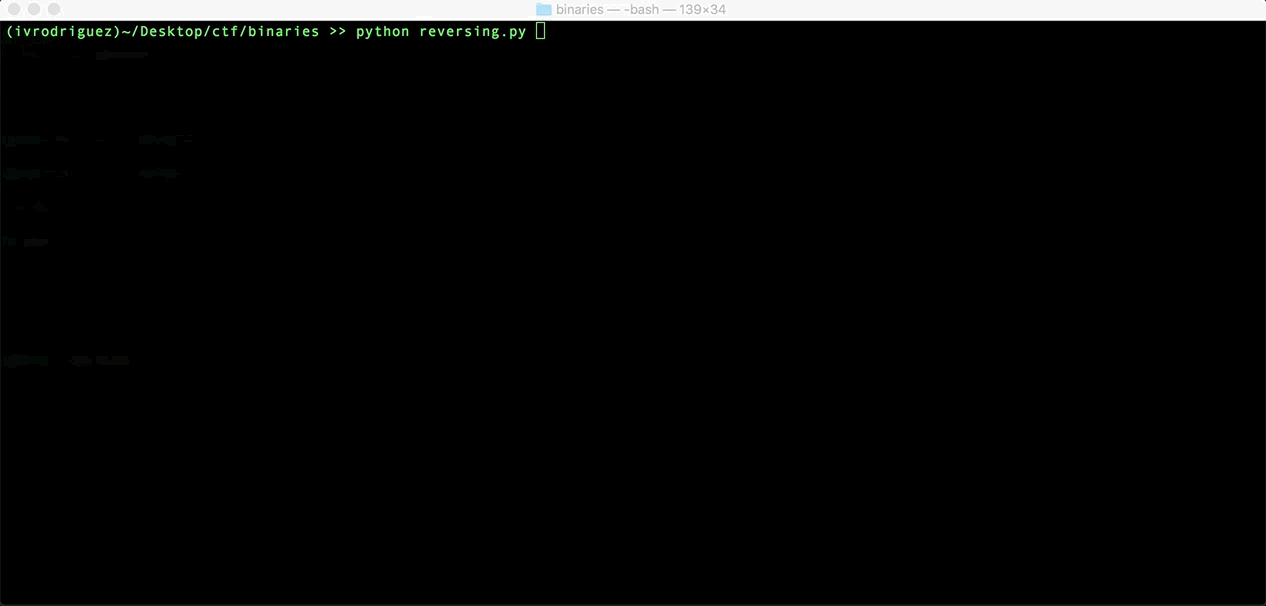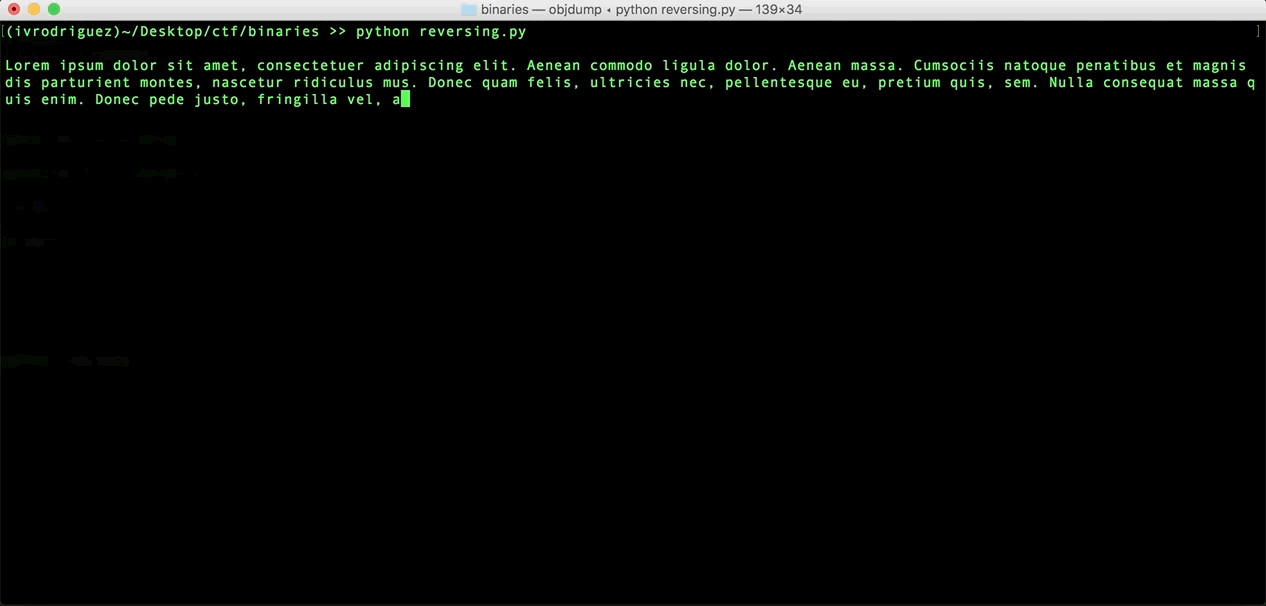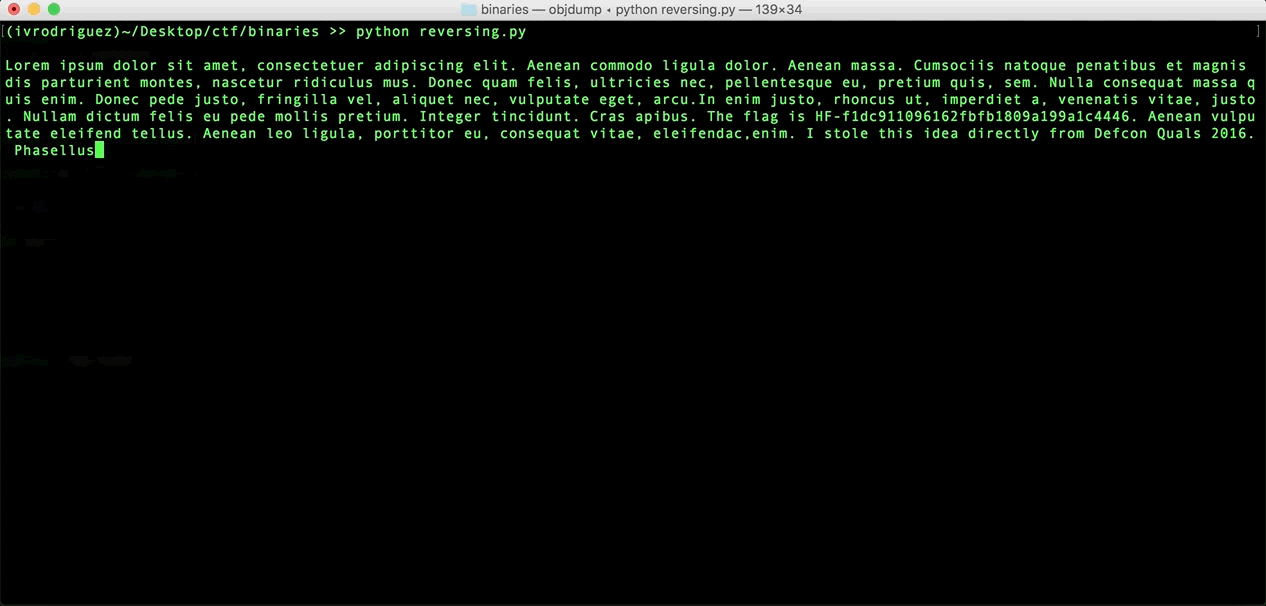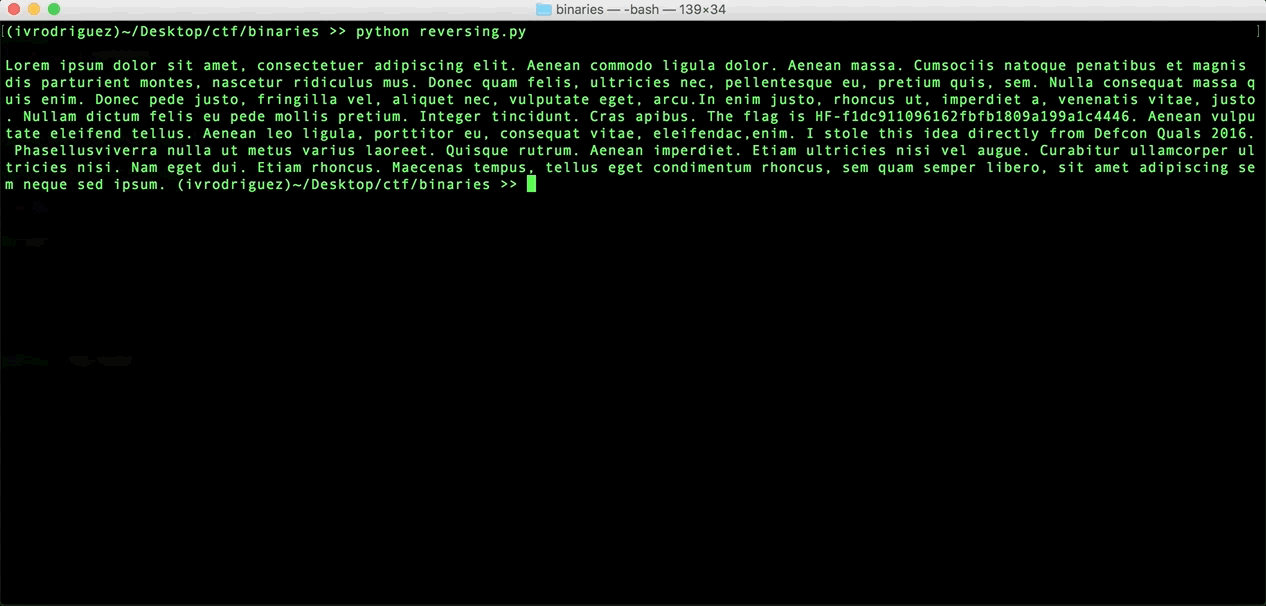
Here you can see the flag: